Ieri il team di Cado Security ha rilasciato un nuovo report relativo ad un nuovo malware che, oltre ad infettare i sistemi e minare Monero (XMR), ruba anche le credenziali AWS (Amazon Web Service).
New blog! We saw a worm spreading over the weekend that steals AWS Credentials – the first we've seen with that capability. It also scans and exploits vulnerable Docker & Kubernetes systems https://t.co/PhDZpQL4GU pic.twitter.com/RQfQsJB2ME
— Cado (@CadoSecurity) August 17, 2020
Negli ultimi anni le società stanno passando gradualmente da sistemi interni di gestione delle risorse informatiche a sistemi esterni per potervi accedere da remoto e abbassare i costi sia di acquisto dei materiali che di manutenzione.
Questo si è tradotto in una forte crescita nel settore cloud computing, per cui l’azienda prende in prestito risorse computazionali e ci costruisce sopra la propria piattaforma che utilizzerà, come se fossero computer virtuali.
Purtroppo un aspetto pericoloso di questo sistema è il fatto che una volta entrati nel sistema, a cascata vengono compromessi tutti i sistemi della rete senza che si possa intervenire, dato che una delle soluzioni è quella di resettare i vari sistemi e sperare di non aver perso nulla.
Il team di ricerca ha scoperto che dietro questo malware si cela un gruppo criminale che si fa chiamare TeamTNT, che ha compromesso diversi Docker e Kubernetes.
Una volta attaccato un device i criminali hanno vanno alla ricerca della cartella “.aws/credentials” e “.aws/config” e mandano i file ad un server dei criminali sayhi.bplace.net. quando ciò avviene il server restituisce la scritta THX, ossia thanks in inglese.
Da quello che si è scoperto le relative credenziali vengono inserite successivamente in maniera manuale da parte dei criminali, quindi questo può essere un vantaggio perché agendo in tempo e cambiandole la vittima potrebbe aggirare il sistema.
Inoltre, il team di Cado Security ha coperto che il malware contiene anche il codice del famigerato Kinsing, che permette di fermare il tool di sicurezza Alibaba Cloud.
Dopo aver rubato le credenziali, il malware non si ferma qui ma procede ad installare il mining tool XMRig.
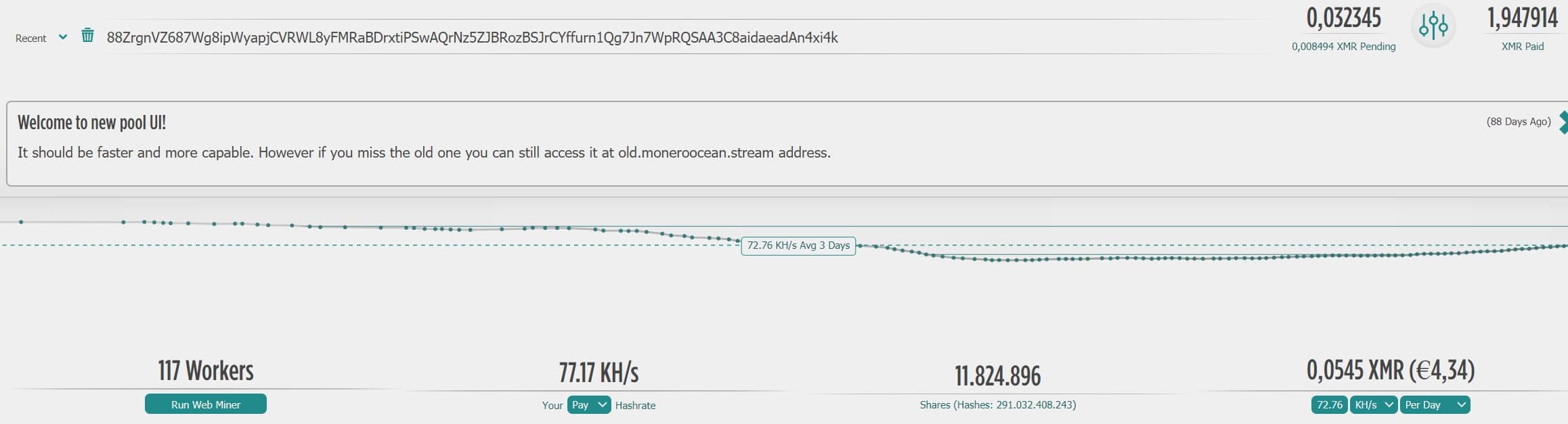
Dalla ricerca si è scoperto che almeno 119 sistemi sono già stati compromessi e sono stati scoperti 2 indirizzi Monero associati ai criminali:
88ZrgnVZ687Wg8ipWyapjCVRWL8yFMRaBDrxtiPSwAQrNz5ZJBRozBSJrCYffurn1Qg7Jn7WpRQSAA3C8aidaeadAn4xi4k in monero ocean.
Questi generano circa €4 al giorno ossia 0,054 XMR al giorno ed i criminali hanno già incassato quasi 2 XMR.
Il report si conclude con alcuni consigli sul come, ad esempio, sarebbe saggio eliminare le cartelle delle credenziali, utilizzare un firewall che limita l’accesso alla API del Docker, controllare il traffico inviato ad eventuali mining pool e controllare se ci sono connessioni a pagine http.



