Yesterday, a group of hackers managed to steal about 200 bitcoins (BTC) with a phishing attack aimed at users of Electrum wallets.
Wallets like Electrum, in order to be quick to install and use, do not store the entire blockchain but connect to servers.
Hackers have created fake wallet-compatible servers and have waited for some unsuspecting user to use them without noticing the connection to the fake servers.
When the user made a transaction, the fake server did not allow the validation and responded with an error message that invited to download another version of the wallet passing it off as an update.
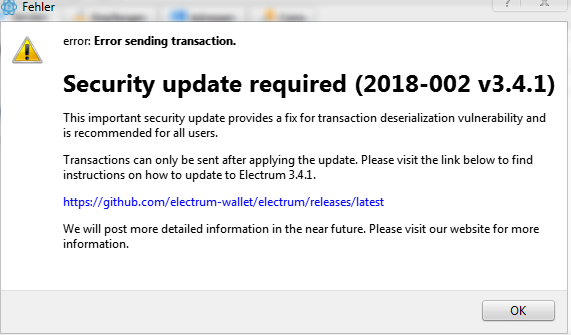
More experienced users have noticed the phishing attempt because Electrum never requires an update, and above all does not invite users to download new versions by proposing a link.
Moreover, the link provided by the hackers did not redirect to the official website of Electrum but to another domain. Many inexperienced users fell for it.
The new version of the wallet, in fact, was another software developed by hackers to make the users write and send their wallet seed: in this way the unsuspecting users voluntarily provided the seed of their wallet to the attackers, who immediately used it to steal all the BTCs contained in it.
In total it seems that the attack has yielded about 200 bitcoins, for an equivalent value of almost a million dollars.
The attack was also confirmed on Electrum’s official Twitter profile, with a screenshot of the fake message inviting users to download the updated version from a link on GitHub that doesn’t match that of the wallet’s official website.
There is an ongoing phishing attack against Electrum users. Our official website is https://t.co/aHiZIZH54e Do not download Electrum from any other source. More on the attack here: https://t.co/x5mPVspKfO
— Electrum (@ElectrumWallet) December 27, 2018
The attack seems to have started on December 21st. Now the fake Electrum GitHub account has been blocked and the malicious files have been removed.
To make sure you have installed the latest correct version of the wallet just proceed to a new installation.
The original software, in fact, was not affected or violated by the attack: it would have been enough not to install the fake version to not have any kind of problem.
However, a new version is expected in order to prevent similar attacks.




